CryptoLocker: an in-depth analysis of the pioneering ransomware
CryptoLocker, synonymous with the evolution of ransomware, emerged as a significant threat in the cyber landscape. Its method of encrypting victims' files and demanding ransoms for decryption heralded a new era of cyber-attacks. This analysis delves deep into CryptoLocker's history, operational mechanisms, various versions, and its overarching impact on cybersecurity.
1. History of appearance
CryptoLocker made its debut in September 2013, spreading primarily through malicious email attachments. These emails are often masqueraded as legitimate communications from reputable sources, enticing unsuspecting users to run the malware.
Furthermore, the Gameover ZeuS botnet, a notorious malware network infamous for stealing banking credentials, played a crucial role in boosting CryptoLocker's distribution. This two-fold distribution strategy ensured a swift and extensive infection rate.
2. Technical breakdown of CryptoLocker's operation
CryptoLocker's primary distribution method was through email attachments that appeared to be from legitimate companies. These attachments often contained a ZIP file, which, when opened, revealed an executable disguised as a PDF file. This deceptive tactic took advantage of Windows' default behavior of hiding file extensions.
Upon execution, CryptoLocker would install itself in the user's profile folder and modify the registry to ensure it ran on every system startup. It would then establish a connection with its command and control servers. These servers would generate a 2048-bit RSA key pair, sending the public key to the infected machine. The malware would then proceed to encrypt files with specific extensions, including but not limited to Microsoft Office documents, OpenDocument files, images, and AutoCAD files.
Encryption mechanism:
Upon activation, CryptoLocker sought a connection to its command and control (C2) server. This connection facilitated the generation of a unique RSA-2048 key pair: a public key dispatched to the victim's system for file encryption and a private key retained on the attacker's server for potential decryption.
Targeted file extensions:
CryptoLocker was indiscriminate in its approach, targeting a vast array of file extensions, from common document formats like .doc and .pdf to multimedia files and database files. This ensured a crippling impact on the victim, both personally and professionally.
Ransom communication:
Post encryption, victims were greeted with a ransom note detailing the payment method (usually Bitcoin or other cryptocurrencies) and a countdown timer, typically set at 72 hours. Failure to comply within this window either escalated the ransom amount or led to the permanent deletion of the decryption key.
3. ILOVEYOU virus and its connection to CryptoLocker
In May 2000, the digital realm was disrupted by the ILOVEYOU virus, a malware that spread rapidly through email. Originating from the Philippines, the virus enticed recipients with an "ILOVEYOU" subject line and a seemingly benign attachment. Upon opening, the virus activated, causing widespread damage and resulting in billions in financial losses. Drawing parallels with CryptoLocker, both malware utilized email as a primary distribution method. ILOVEYOU relied on social engineering, while CryptoLocker used deceptive business correspondence. Both had vast global impacts, highlighting vulnerabilities in digital ecosystems. However, their intentions varied. ILOVEYOU aimed for propagation and disruption, whereas CryptoLocker evolved to focus on financial extortion.
The ILOVEYOU incident catalyzed a significant shift in cybersecurity awareness. It underscored the importance of stringent email filtering, timely software updates, and comprehensive user education. This heightened cybersecurity posture posed challenges for subsequent threats like CryptoLocker. Yet, as demonstrated by CryptoLocker's success, cyber adversaries continued to refine their tactics, underscoring the perpetual dynamics between cyber threats and defense mechanisms.
4. Evolution of CryptoLocker: versions and variants
CryptoLocker's success inevitably led to the emergence of various versions and imitations:
|
|
Original CryptoLocker (2013)
The pioneer that set the stage. It primarily spread through malicious email attachments and leveraged the Gameover ZeuS botnet for wider distribution. Upon execution, it connected to its command and control server to generate a unique RSA-2048 key pair for encryption.
|
|
|
CryptoLocker 2.0
Not a direct successor of the original, but rather a variant inspired by it. Developed in C#, it differed from the original's C++ codebase. While it retained the ransomware blueprint, it introduced a different encryption methodology.
|
|
|
CryptoLocker 3.0
An advanced iteration that showcased a more sophisticated payment portal, offering victims a streamlined user experience. It also introduced multi-language support, catering to a broader global victim base.
|
|
|
CryptoLocker 2015
Emerging in early 2015, this version was initially perceived as a resurgence of the original CryptoLocker. However, detailed analysis revealed it as a distinct variant. While it maintained the core ransomware blueprint, it incorporated more aggressive propagation techniques and a refined encryption process. The user interface for its ransom note was also enhanced, reflecting the evolution in ransomware design.
|
|
|
TorrentLocker
Borrowing heavily from CryptoLocker's playbook, especially in its ransom communication, this variant primarily propagated via geographically targeted spam campaigns.
|
|
|
CryptoDefense and CryptoWall
These successors, inspired by CryptoLocker, introduced their unique features while retaining the core ransomware blueprint. For instance, CryptoWall incorporated advanced evasion techniques to bypass traditional security solutions.
|
5. How much money did CryptoLocker make?
Conservative estimates suggest that the operators behind CryptoLocker extorted around $3 million from their victims. However, a more granular analysis conducted by ZDNet in December 2013 traced four specific bitcoin addresses linked to CryptoLocker ransom payments. The transactions associated with these addresses amounted to 41,928 BTC between October and December of that year. Given the average bitcoin value during that period, this translated to approximately $27 million. It's worth noting that these figures only represent a subset of the total transactions, as not all victims would have used the tracked bitcoin addresses.
Beyond the direct ransom payments, the indirect costs associated with CryptoLocker attacks were substantial. These include costs related to system downtime, loss of productivity, data recovery efforts, IT consulting, and reputational damage. For businesses, especially those without recent backups or those that faced prolonged encryption of critical data, the financial ramifications could be long-lasting.
The success of CryptoLocker also had broader economic implications. Its profitability inspired a slew of copycat ransomware campaigns, leading to an increase in the demand for cryptocurrencies like bitcoin and driving their prices up. Additionally, the rise in ransomware attacks spurred growth in the cybersecurity industry, with businesses and individuals seeking more advanced protection mechanisms.
|
|
Screenshots
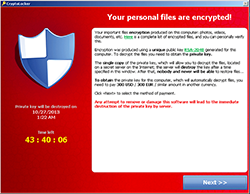
Original CryptoLocker (2013)
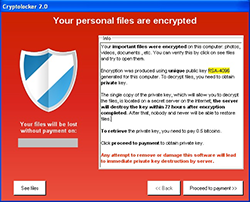
CryptoLocker 2.0
|
6. Countermeasures, mitigation, and takedown
The widespread impact of CryptoLocker prompted a coordinated response from both the cybersecurity community and law enforcement agencies. By June 2014, a significant blow was dealt to the ransomware's operations through the launch of Operation Tovar. This operation was not a solitary endeavor but rather a collaborative effort that saw participation from global law enforcement agencies, including the FBI, Interpol, and Europol, as well as prominent cybersecurity firms.
The primary objective of Operation Tovar was to target and dismantle the Gameover ZeuS botnet. This botnet was not just another malicious network; it was the primary distribution mechanism for CryptoLocker. By neutralizing Gameover ZeuS, the operation effectively severed CryptoLocker's primary mode of propagation, thereby limiting its ability to infect new systems.
While the takedown of the botnet was a significant achievement, the challenge of dealing with already infected systems remained. Recognizing this, cybersecurity researchers embarked on a detailed analysis of CryptoLocker's architecture. Their efforts bore fruit when they identified certain vulnerabilities and oversights in the ransomware's design. Capitalizing on these weak points, researchers managed to access and retrieve a subset of the private decryption keys that the ransomware used to encrypt victims' files.
Securing these decryption keys marked a pivotal moment in the battle against CryptoLocker. This breakthrough facilitated the creation of online decryption utilities, which were promptly disseminated to the public domain. Affected entities could leverage these utilities to decrypt their compromised files, negating the need to meet ransom demands. This development not only alleviated the distress of numerous individuals and enterprises but also underscored the cybersecurity community's tenacity and capability, sending a definitive signal to cyber adversaries.
7. CryptoLocker 2015 analysis
When CryptoLocker 2015 first made its appearance, many in the cybersecurity community believed it to be a direct continuation of the original 2013 CryptoLocker threat due to shared naming and basic encryption-ransom methodologies. However, a deeper analysis quickly revealed that this was not merely a resurgence of the old threat but a variant with distinct operational differences.
One of the standout features of CryptoLocker 2015 was its refined encryption techniques. It expanded its range of targeted file extensions and showcased more aggressive propagation methods. These methods were not limited to traditional vectors but leveraged sophisticated phishing campaigns, indicating a shift in tactics. Another notable change was in the ransom note's user interface. The 2015 variant presented victims with a polished and intuitive interface, a clear departure from its predecessor. This improvement suggested a deliberate attempt to streamline the ransom payment process, ensuring victims could navigate the demands with minimal confusion.
In terms of distribution, while the original CryptoLocker was heavily dependent on the Gameover ZeuS botnet, the 2015 version demonstrated versatility. It explored a variety of distribution channels, from exploit kits to malicious advertisements, and even ventured into social engineering tactics on social media platforms. This adaptability highlighted the evolving nature of ransomware threats and their ability to pivot based on the cybersecurity landscape.
The response from the cybersecurity community to CryptoLocker 2015 was swift, informed by prior encounters with the original variant. Advanced threat detection tools were deployed, and user awareness campaigns were ramped up, reflecting a proactive approach to this renewed threat. In conclusion, CryptoLocker 2015, while drawing heavily from the legacy of its predecessor, carved its own niche in the ransomware domain, emphasizing the need for continuous vigilance in the face of evolving cyber threats.
8. Legacy, contemporary relevance, and lessons learned
CryptoLocker's ramifications extend beyond its immediate victims. It catalyzed a paradigm shift in cybercriminal strategies, with ransomware becoming a favored tool for monetization.
Key takeaways from the CryptoLocker saga include:
Backup imperative:
The importance of maintaining regular, isolated backups cannot be overstated. Such backups can render ransomware attacks ineffective.
Email hygiene:
Exercising caution with email attachments, especially from unknown senders, is crucial. Employing advanced email filtering solutions can further mitigate risks.
Patch management:
Keeping operating systems and software updated ensures known vulnerabilities are addressed, reducing potential attack vectors.
Advanced threat detection:
Traditional antivirus solutions proved inadequate against CryptoLocker. This underscored the need for advanced threat detection and response tools capable of identifying and neutralizing sophisticated threats.
To recap
CryptoLocker, in its brief yet impactful existence, reshaped the cybersecurity landscape. Its legacy serves as a constant reminder of the evolving nature of cyber threats and the imperative for proactive, layered defense strategies. As we navigate the digital age, understanding and learning from past threats like CryptoLocker equips us to better face future challenges.
|
